Introduction: A New Predator Appears
Every so often, a new ransomware crew makes its debut. Most of the time, they look like recycled versions of existing groups, running the same playbook with a different ransom note. But during a recent incident response engagement, Dark Entry IR Team came across something different — a new group going by the name of DireWolf.
The group first known attack is marked May 2025, and the incident we invistigated occurd in June 2025. There were no existing write-ups, no IOCs to pull from, no breadcrumbs in open-source intelligence. Just a set of fresh tracks left by attackers who clearly wanted to make their mark. This post is our field report on DireWolf: their playbook, the tools they used, and the techniques they employed during their campaign.
How it all started:
One of the impacted organizations — targeted by the DireWolf ransomware operation — retained our incident response team to perform threat eradication, vulnerability remediation, and implementation of defensive measures to prevent recurrence. The same day, Dark Entry IR team moved-in, phsyically, to the client premises for immediate support.
Due to the ransomware group encrypting every domain connected device, including the servers, and client have as well re-installed many devices, it was quit hard to recover IOC's of the group ... at the begaining of the investigation. However, during the incident responce process, our team managed to trackdown the servers, IPs, C2's, URL's and tools used by DireWolf team.
What happened during the actual incident will follow below, only what we are allowed to mention based on the client's request. But before that, this is how the group operates:
-
DireWolf operators chooses any famouse software, newly released game, often searched tool and so on.
-
Bind their malware loader with the legitimate software as a Crack, KeyGenerator, DLL file or game launcher.
-
Publish the infected software (game or tool) in every possible source they can reach, such as forums, torrent, software downloads sites, Telegram groups and so on (Spray and Pray).
-
Once the mass infection happens using the cracked software, an info-stealer is installed on the infected devices which steals credentials, credit cards, browser cookies/history and configuration files.
- All the stolen data are then uploaded to DireWolf servers, ready to be searched for valuable targets.
- DireWolf would then use the huge amount of stolen credentials to search for their targeted organisation by targeting the corporate domains of the companies and not the public sites (i.e. uberinternal.com, pubgcorp.com, fileshare.<OrgName>.TLD
- Once they confirm infection of a valuable target where they have the info-stealer data and the malware loader already installed on the Org employee device, the Operation start..
Initial Access: Cracks in the Armor
DireWolf’s entry point to our IR client wasn’t exotic. They gained their first foothold through cracked software installed on IT administrator machines. Three workstations were affected — and unfortunately, two of them had cached Domain Admin credentials.
With that, DireWolf had a privileged position in the network before they even started moving.
Persistence & Backdooring
Once inside, the attackers planted multiple persistence mechanisms:
-
They created a Windows service that executed
Loader.exe.
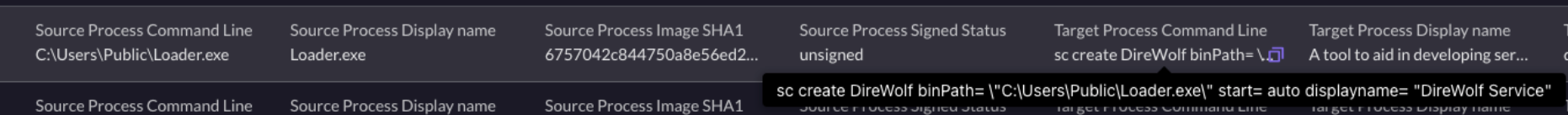
-
They scheduled recurring tasks to reinvoke their loader.
-
They updated registry keys so that PowerShell would auto-execute callbacks to their C2 servers.
-
They even tampered with the Windows Boot Configuration, forcing systems into minimal boot mode to evade SentinelOne’s EDR processes, which indeed wasnt detected by SentinelOne during the incident.

This layered persistence ensured that even after cleanup attempts, DireWolf could reappear — which is exactly what happened when the client tried to restore from backups.
Lateral Movement: VNC and Domain Control
With Domain Admin creds in hand, DireWolf moved laterally into the Domain Controller. For non-domain machines, they exploited a misconfigured VNC deployment that was running across the environment.
From the DC, they created new Group Policy Objects (GPOs) to distribute malware to every reachable endpoint in order to encrypt it using their Ransomware.
The Arsenal
DireWolf’s deployment used a toolkit of files, staged and executed through GPOs and loaders:
AutoUpdate.exe- A malware loader that is only used to download and execute further malwares from their C2. Note that they used steamcommunity.com as their C2. The loader visits a pre-configured user profile, identify the base64 code in the profile descricription and decodes it, it shows a URL that would be downloaded and executed.-
run.bat– a script to pull and launch additional malware, includingLoader.exe. It is also used to tamper with the Boot Configuration and run it in the SafeBoot Minimal mode, and more. See below: 
-
Loader.exe– the dropper that fetched payloads and set up persistence. -
fastenc.exe– the ransomware binary itself, running with SYSTEM privileges to encrypt files. -
rhc.exe– a helper tool used to execute other binaries (notably the stealer components) invisibly. -
php.exe(legitimate PHP binary) – abused to execute a bundledindex.phppayload. -
index.php– contained the credential stealer code, which harvested browser-stored passwords and exfiltrated them. -
GPODistributionSystem.exe– forced immediate Group Policy updates to spread malware faster.
This arsenal gave DireWolf full control: they could steal credentials, spread rapidly, encrypt at scale, and persist through cleanup attempts.

Data Theft & The Backup Trap
Before encryption began, DireWolf quietly exfiltrated a huge amount of documents (75GB) from the company’s fileshare server. This gave them the leverage for a double-extortion scheme: pay or your stolen data gets leaked.
But what really set them apart was how they sabotaged recovery.
Our client had offline backups — a lifeline in most ransomware cases. But every attempt to restore data ended in re-encryption. Why? Because DireWolf’s persistence mechanisms (services, scheduled tasks, registry callbacks) re-triggered their loaders after restore.
Instead of just deleting backups, they poisoned the restore process itself, ensuring victims felt trapped and cornered.
Encryption & Ransom Note
Once backups were crippled and data stolen, DireWolf unleashed fastenc.exe across the environment. The binary encrypted system files as well as business-critical documents (.pdf, .docx, .csv, .xlsx, .ppt), leaving machines unusable.
Finally, they dropped ransom notes named HowToRecoveryFiles.txt into every folder. The note promised that unless the company engaged with their Tor-based negotiation portal within three days, stolen data would be leaked publicly.
Why DireWolf Matters
DireWolf may not (yet) have the name recognition of LockBit or ALPHV, but their playbook shows a dangerous mix of pragmatism and cruelty:
-
Pragmatism: using cracked software, cached credentials, and VNC misconfigs to get in.
-
Cruelty: sabotaging backups so recovery became a cycle of false hope.
They don’t appear to be innovating at the technical level (except for the Boot configuration update part), but they are innovating at the psychological level — breaking one of the last defenses organizations trust most: their backups.
DireWolf - OPSEC Playbook & TradeCraft:
-
The threat actors routinely abused legitimate binaries (e.g., php.exe, Node.js) — a misuse pattern Microsoft documented in mid-April 2025: https://www.microsoft.com/en-us/security/blog/2025/04/15/threat-actors-misuse-node-js-to-deliver-malware-and-other-malicious-payloads/
- Most payloads were executed in memory, minimizing disk artifacts. They also employed Boot Configuration tampering to bypass SentinelOne EDR. The technique is detailed here.
- To avoid detection by Threat Intelligence / SOC teams, their C2 only responded to requests containing a custom HTTP header X-Machine-Id set to the target’s MachineGUID; otherwise the server returned a 404. The MachineGUID can be obtained on Windows with PowerShell, for example:
$GUID = Get-RegistryValue "HKLM:\SOFTWARE\Microsoft\Cryptography" "MachineGuid" - If the request is correct, and contains the required header, the following PowerShell code is returned: https://github.com/darkentryams/direwolf-ransomware-group/blob/main/DireWolf-C2-Response.txt

DireWolf - Infrastructure Trackdown:
The tools they are using since May, 2025, can be downloaded on our Dark Entry's Github Repo at: https://github.com/darkentryams/direwolf-ransomware-group
And although they made sure to delete all their tracks and tools, our team at Dark Entry was able to trackdown their infrastructure and obtain most of the tools used during the operation.
Warning, the following is still ALIVE.



Indicators of Compromise (IOCs):
It was not possible to obtain copies of multiple artifacts: the adversary deleted most on-disk artifacts, executed payloads in memory (minimizing disk footprint), performed full-disk/file-system encryption, and forced reboots—preventing forensic capture of live data. However, we managed to access one of their servers which contained multiple of their used tools, and are listed as following.
Key Filenames & Hashes:
rhc.exe - 22e7528e56dffaa26cfe722994655686c90824b13eb51184abfe44d4e95d473findex.php - a9a467842fa1143cbfa9db8ebd38eff0b725ec5e110be1eae0c4af9956a50a95-
rhc.ext/php_ioncube.dll - 4b6f679ab3da317ee310d5bd482b41a77f5ebf1fc0d514d3595c3d16db6e7327 -
Dropped File 1 - 2e7de45331e31fa09a01e032e561be4063f0a0989d6873bd68a70ccabc2295f9 -
Dropped File 2 - 1c1ef5f2c13da4e6399a1d1b4600dfc474c3a74447fdff219f0df449e4da908c -
PkgdefMgmt.dll - 25e0995a5093c57dc452be8848c060e19faecc8bed16743773abf50d84e28b78 -
ext/php_bz2.dll - d1457076b72d629f0af7e98cd6fe5be4fb0b18fb9c15675f2995b4c5e88a8106 -
ext/php_com_dotnet.dll - e7acc5942596b3dcdb7c31fcbd648f7aa6a6a512332930a48e543d818d6c8125 -
ext/php_curl.dll - 05c99429e208bc9f345c791e16dd3f68ec628186d64e2acbc7f2f6dcc877bf11 -
ext/php_fileinfo.dll - 1132e7e1cd973f0d44da001bc64ac36a061b69192c9d8ea175cd73e94100bcc0 -
ext/php_gd2.dll - ddc10933f9d057fbb929f59997f5913182ce928dc8ffad8963eed74c2ef50256 -
ext/php_mbstring.dll - 6653e52f3a7d12afc5e1d5922a73d56a9d914864a1f882004e986ea210005b61 -
ext/php_openssl.dll - 673596e0945d61b3f5ff71d293ff8c2cc38464142bdde00387a87ea9af646aed -
ext/php_pdo_sqlite.dll - 8b46ab99dad214f30ff11daf08d6b77041165875a04b3d4dc16cdfcfe73ca625 -
libeay32.dll - fe5ceefedcec83d40bd63a7cc2d4ae4012b3f59f1098638056fdc1a477d405f7 -
libssh2.dll - ed0db696c2ae8b896eab6fd8c71e5fa4c88e6a90b98fffc354593288d59fe119 -
msvcr110.dll - b30160e759115e24425b9bcdf606ef6ebce4657487525ede7f1ac40b90ff7e49 -
phar.phar.bat - ef0f0bd1e919ee96c7d20547f7a823218cd73452f36c47d1a22f2726d5d64308 -
pharcommand.phar - df648729c62124490ae5222f0101c19ee6b3149e52f04b2f098178d0a4fbdaf5 -
php.exe - 702d09e982e2af6bf5d828bb1d27bd3a48efcab7cf8837b023953354c4026550 -
php5.dll - 36179be42a85e363099ab57852f6fd1cd12e602e1475841ab169d13fc8955065 -
ssleay32.dll - df5ca94869c6532d6db6c2aafddc4eab93e867670ce5964728248df68e07ce20 -
Loader.exe -
fastenc.exe -
GPODistributionSystem.exe
URLs:
-
http://dl.benchiu.top/test2.bin -
http://jabastore.gr/t/c.heb -
http://provijhq.top/test2.zip -
http://provijhq.top/test2.txt -
https://www.albumcallgirl.top/test2.txt -
https://www.albumcallgirl.top/test2.zip
Hostnames:
We strongly recommend blocking the entire .top TLD within corporate networks, unless there is a documented business need to allow access.
-
firewall-813.com -
18-22-59.com -
cfpro.top -
jabastore.gr -
kitoto.top -
miloto.top -
roato.top -
roboviso.top -
michaleballack.top -
fp2e7a.wpc.2be4.phicdn.net -
a.wpc.2be4.phicdn.net -
1bilionupdated.top -
1bilionupdateapp.top -
1bilionupdates.top -
dashong.top -
provijhq.top -
albumcallgirl.top -
benchiu.top -
narlovi.top -
zimoe.top -
brove.top -
harnove.top -
birsarke.top -
ostimatu.top -
tonava.top -
domain1.top -
leakonlyfan.top -
videocallgirl.top -
xvideocallgirl.top -
100minion.top -
10minions.top -
10minion.top -
ytb88.top -
msgclick.top -
segarkojiri.top -
bestcontenttool.top -
uncaveclock.top -
api.9share.top -
krisya.top -
opuinues.top -
googleads1.top -
hat-kett.com -
cineastspleet.top
IPs
Note: The group used a mix of Cloudflare-hosted IPs and non-Cloudflare IPs to obscure their infrastructure. Below are some of the non-Cloudflare IPs, along with a few Cloudflare examples. Many other Cloudflare IPs were also used.
Non-Cloudflare IPs:
-
75.2.115.196 -
188.114.96.0 -
20.190.155.65 -
23.195.81.34 -
20.190.155.3 -
20.211.142.181 -
13.64.180.106 -
20.114.59.183 -
20.163.45.183 -
23.59.183.74 -
52.167.17.97 -
20.44.239.154
Cloudflare IP examples:
-
104.21.16.44 -
104.21.17.185 -
172.67.129.20 -
172.67.135.41
Note: Many additional Cloudflare IPs were also used to hide the true hosting infrastructure.
Closing Thoughts
If there’s one lesson here, it’s this: backups are not enough if persistence isn’t eradicated. Before restoring, organizations must ensure attackers are gone — otherwise, recovery just resets the encryption cycle.
This was our first direct encounter with DireWolf. We’ve documented as much as possible to help you—and other organizations—better protect your networks against DireWolf and similar groups.
As always, the Dark Entry team is here to support you. You can reach us at: team<@>darkentry.net
Thank you, and stay safe!